Two-step verification in Plone 4 using login codes sent by SMS.
Project description
Two-step verification for Plone 4 with use login codes sent by SMS. This app allows users to enable the two-step verification for their Plone accounts. A mobile phone with ability to receive SMS messages is obviously required. Usage of two-step verification is optonal, unless site admins have forced it ( configurable in app control panel). Admins can white-list the IPs, for which the two-step verification would be skipped.
Prerequiresites
Mobile phone which is able to receive SMS messages.
Plone 4 (tested with Plone >= 4.3.1)
Usage
Case 1: Enabling the two-step verification
Pre-conditions: User is not logged into the Plone site, does not yet have two-step verification enabled and has a mobile phone.
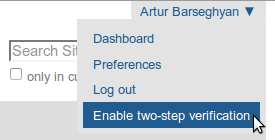
From any page follow the “Enable two-step verification” link in the menu (next to “Log out”).
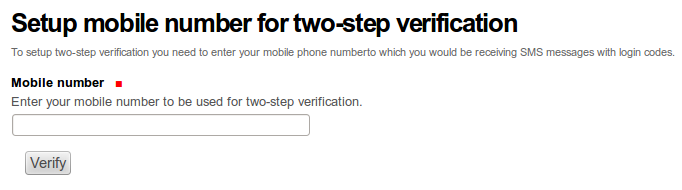
If you haven’t yet filled in your mobile phone number, you will be requested to do so. You will receive immeditely a SMS with confirmation code in.
When you’re done, you get to a page on which you will be requested to enter the code received by SMS.
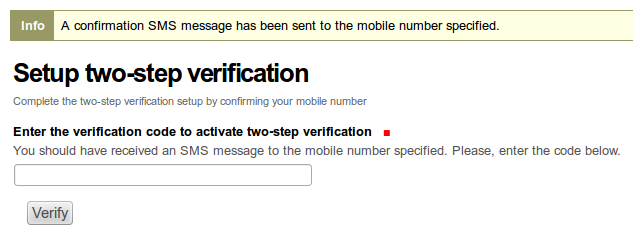
Enter the secret code shown in the “Enter the verification code to activate two-step verification” field for confirmation and press the “Verify” button.
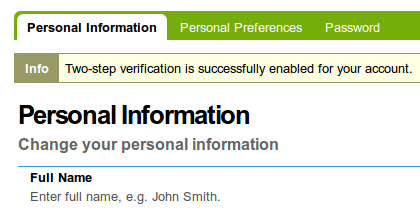
Upon successful confirmation (you should see a message stating that) the two-step verification is enabled for your account.
Case 2: Two-step verification
Pre-conditions: User is not logged in and has enabled the two-step verification.
When you log into the Plone site (just using username and password), you would see an extra screen on which you are asked to provide the login code, sent to your by SMS.
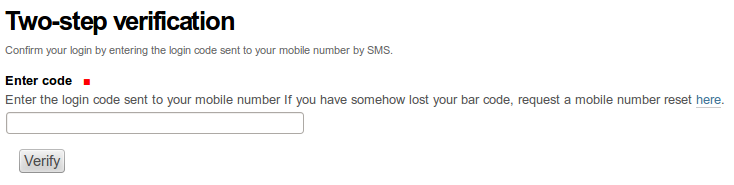
You should then check your phone for the new SMS message and type in the token shown into the “Enter code” field.
If token is valid, you would be logged in.
Case 3: Lost mobile phone or phone number
Pre-conditions: User is not logged in, has enabled the two-step verification.
There might be cases when you have lost your mobile phone (either really lost it or broken accident or somehow lost ownership of your former mobile number). For such cases, you can reset the phone number.
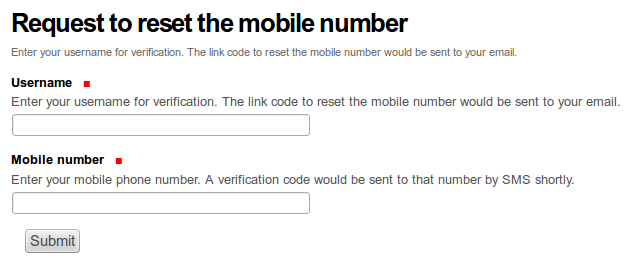
Log into the Plone site (just using username and password), for to see the extra screen on which you are asked to provide the login code, sent to your by SMS and follow the link (help text of the “Enter code” field). You would then land on the page where from you can request the bar code reset.
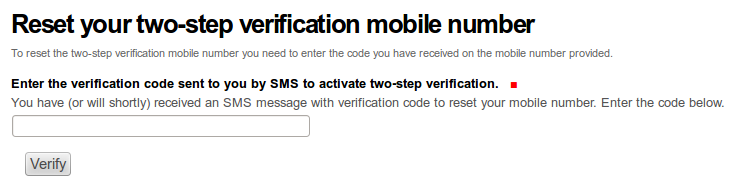
Enter your username and mobile number in the “Username” and “Mobile number” fields respectively, press the “Submit” button. Link for resetting your mobile number will appear in your mailbox shortly. Having clicked on the link to reset the mobile number, would bring your to a page where you can enter the verification code.
You will receive an SMS with verification code shortly. Enter the code in the “Enter the verification code to activate the two-step verification” field.
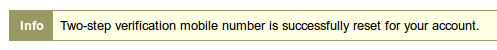
Upon successful confirmation (you should see a message stating that) your bar code is reset.
Case 4: Disabling the two-step verification
Pre-conditions: User is logged in and has enabled the two-step verification.
From any page follow the “Disable two-step verification” link in the menu (next to “Log out”).
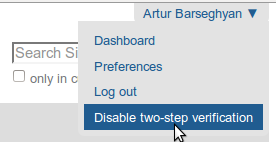
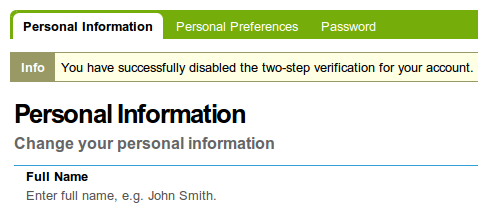
After which you would get a message.
Installation
Buildout
>>> [instance] >>> eggs += >>> collective.smsauthenticator
>>> zcml += >>> collective.smsauthenticator
ZMI
ZMI -> portal_quickinstaller
Choose “SMS Authenticator Plone” and install it.
ZMI -> acl_users
Choose “sms_auth (SMS Authenticator plugin (collective.smsauthenticator))”.
Make sure the “Active plugins” section of “Authentication” has the following plugins in the given order (“sms_auth” should come as first - critical!):
sms_auth
session
source_users
Configuration options
App control panel can be accessed at http://your-plone-site.com/@@sms-authenticator-settings
Main
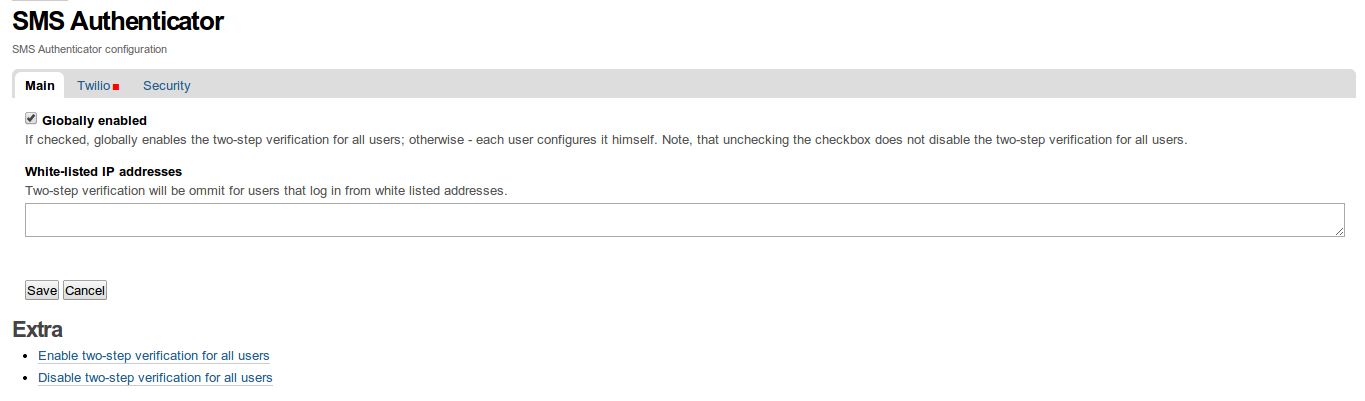
Globally enabled
If checked, two-step verification is globally force-enabled for all site users and they no longer have an option to disable it; this applies to all new users (just registered accounts) as well.
White-listed IP addresses
List of white-listed IP addresses - one at a line. If user comes from one of those, the two-step verification is skipped even if user has enabled it or two-step verification is globally enabled.
Extra
Additionals options of the control panel are:
Enable two-step verification for all users.
Disable two-step verification for all users.
Twilio

Twilio number
Your Twilio AccountSID and AuthToken. Visit your Twilio Account Phone Number page and check the Manage Numbers section.
Twilio AccountSID and Twilio AuthToken
Your Twilio AccountSID and AuthToken. Visit your Twilio Account Settings page and check the API Credentials section.
Security
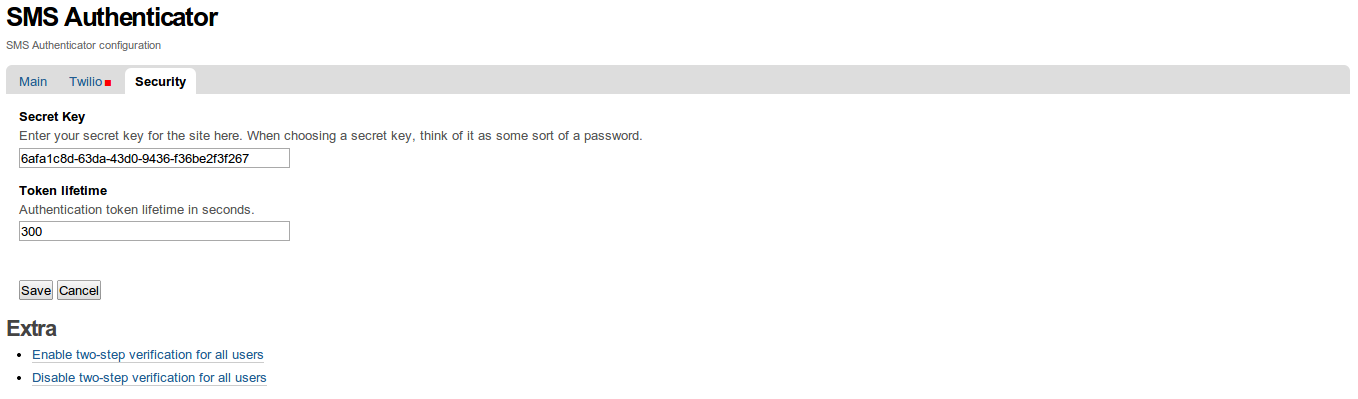
Secret Key
Site secret key - can be any string. See it as some sort of a password.
Token lifetime
Lifetime of the login- and the mobile number reset- codes. Defaults to 5 minutes (300 seconds).
Notes
It’s important that SMS Authenticator comes as first in the ZMI -> acl_users -> Authentication.
Tested in combination with the following products:
The Products.LoginLockout <https://pypi-hypernode.com/pypi/Products.LoginLockout>_. smsauthenticator comes as first, LoginLockout as second. All works fine.
Documentation
See the documentation at:
Support
For feature requests or bugs, open an issue. For questions, send us an email to info@gw20e.com.
License
GPL 2.0
TODOs and Roadmap
See TODOS.rst file for the list of TODOs.
Changelog
0.1
28-02-2014
Initial release, with two-step verification, IP white-listing, configurable lifetime for the login codes, mobile number recover and app control panel.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Hashes for collective.smsauthenticator-0.1.tar.gz
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | b4d8e40bda7875421f8a26a7f47855d473626e49000043d6672f9c6562077402 |
|
| MD5 | 2389b4a6e0475a7fb678739f7aeb4fbb |
|
| BLAKE2b-256 | 4101f27ab6ad8ab3171df96c253a74ccde871499d14f0486988874eee02f687d |













