Checks for vulnerabilities in a running k8s cluster
Project description



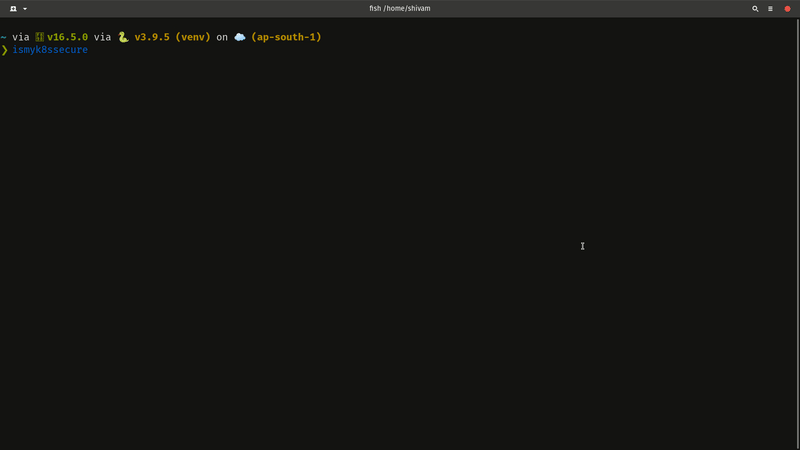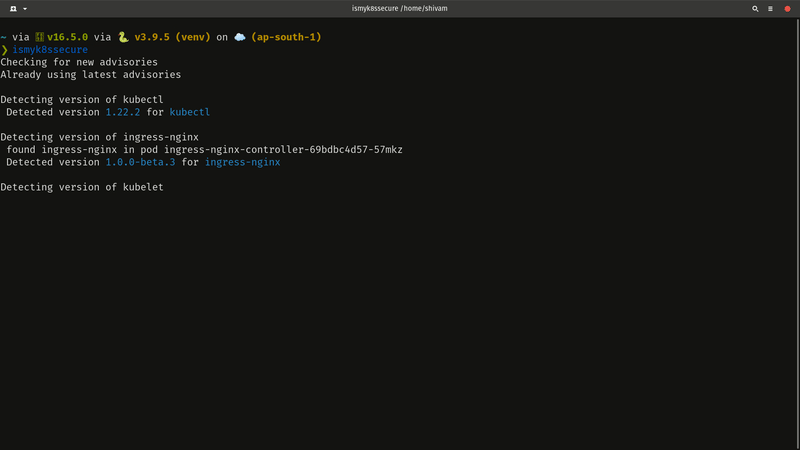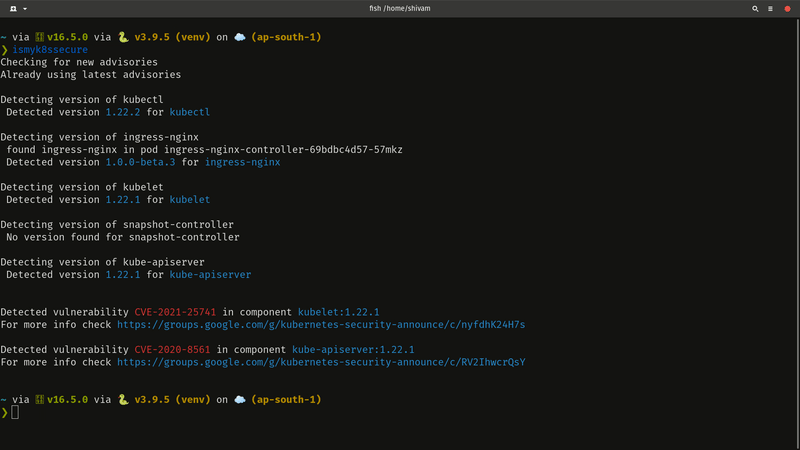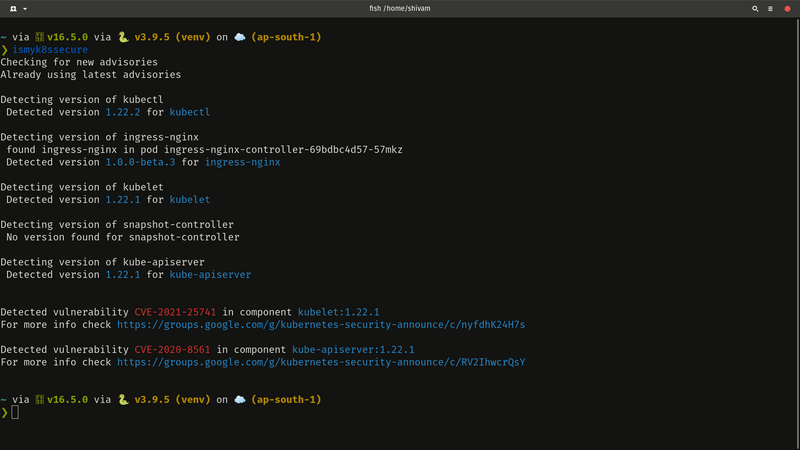
Get Started in 60 seconds !
Make sure you meet the following prerequisites
Prerequisites:
- kubectl is configured to connect to cluster.
- Optional, but highly recommended: make sure you are in a python venv.
Simply run the following commands, and run your first scan.
pip install ismyk8ssecure
ismyk8ssecure
How It Works:
This tool consists of 3 components:
Advisories:
These are yaml files with following schema:
vulnerability_id:
vulnerability_description:
vulnerable_components:
- component_name:
vulnerable_versions: [] # These are computed from `vulnerable_version_ranges`
vulnerable_version_ranges: [] # These are manually filled
references: []
last_updated_at:
created_at:
Advisories can be found in the advisories directory in this repo.
Version Detectors:
These are functions which detects the version of a particular k8s component. See examples in TODO.
Vulnerability Detectors:
These are functions defined per (vulnerability, k8s component) pair. They are called depending upon the results of above 2 components. They verify whether the corresponding "vulnerability" is present in the detected "k8s component".
Roadmap:
-
Convert most of the kubernetes security advisories into machine readable format.
-
Implement fine tuned vulnerability detectors and eventually become a smart npm audit.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.











