View and control remote terminals from your browser with end-to-end encryption
Project description

View and control remote terminals from your browser with end-to-end encryption
Documentation: https://cs01.github.io/termpair
Source Code: https://github.com/cs01/termpair
Try It: https://grassfedcode.com/termpair
What is TermPair?
TermPair lets developers securely share and control terminals in real time.
Usage
Start the TermPair server with termpair serve, or use the one already running at https://grassfedcode.com/termpair.
> termpair serve --port 8000
INFO: Started server process [25289]
INFO: Waiting for application startup.
INFO: Application startup complete.
INFO: Uvicorn running on http://localhost:8000 (Press CTRL+C to quit)
INFO: ('127.0.0.1', 51924) - "WebSocket /connect_to_terminal" [accepted]
Then share your terminal by running termpair share:
> termpair share --port 8000
--------------------------------------------------------------------------------
Connection established with end-to-end encryption 🔒
Sharing '/bin/bash' at
http://localhost:8000/?terminal_id=fd96c0f84adc6be776872950e19caecc#GyMlK2LLTqvoyTNzJ+qwLg==
Type 'exit' or close terminal to stop sharing.
--------------------------------------------------------------------------------
You can share that URL with whoever you want. Note that anyone that has it can view and possibly control your terminal.
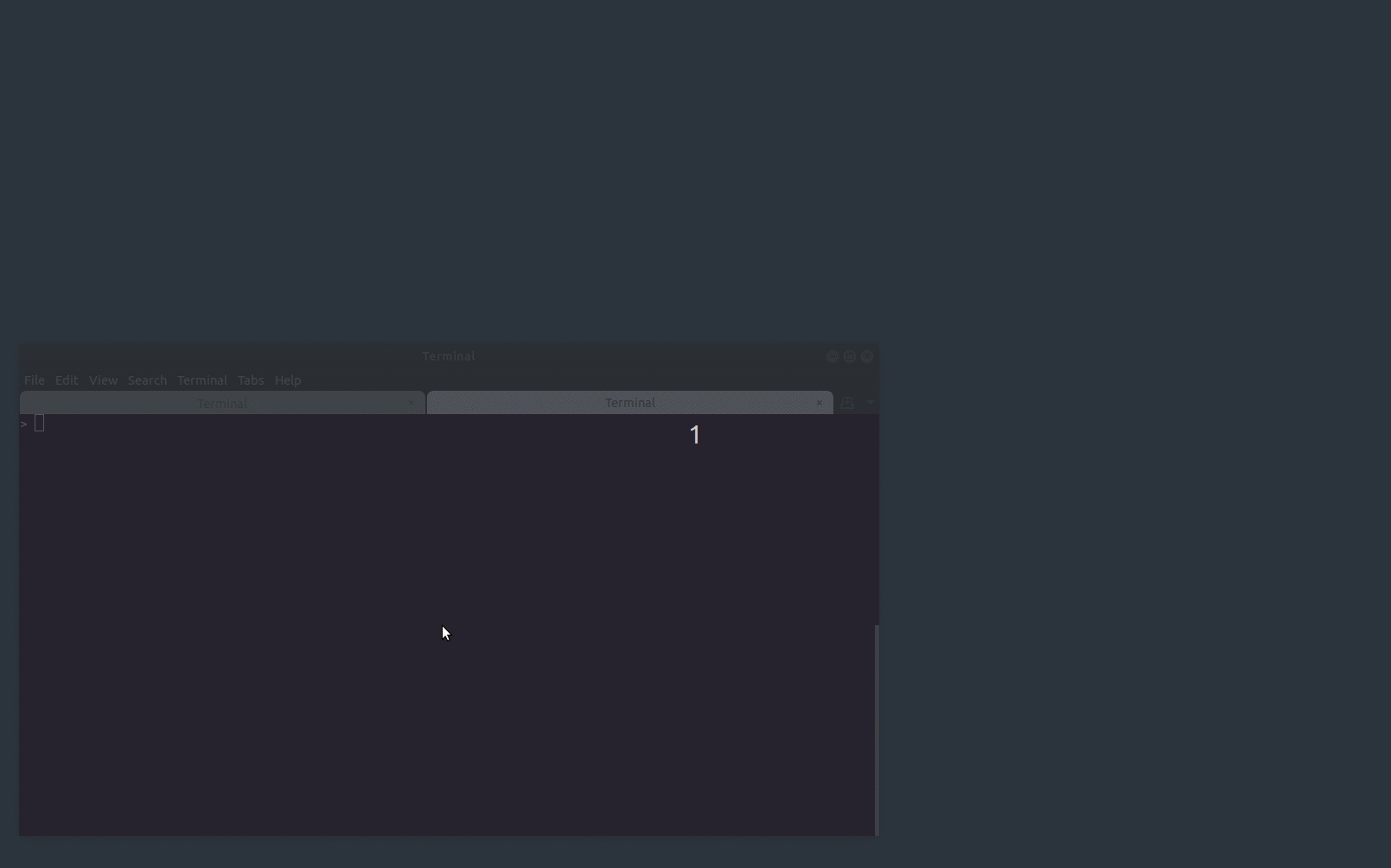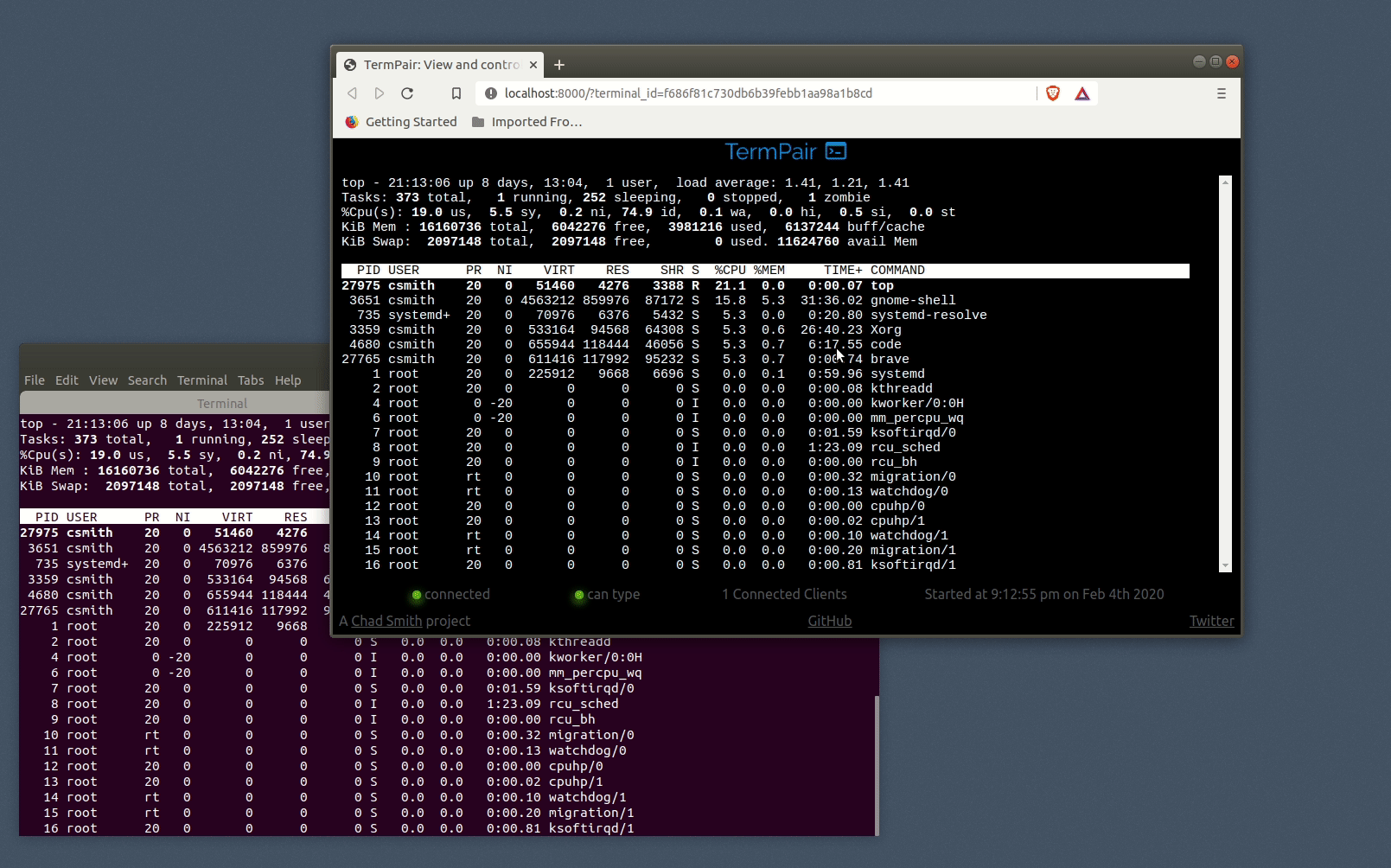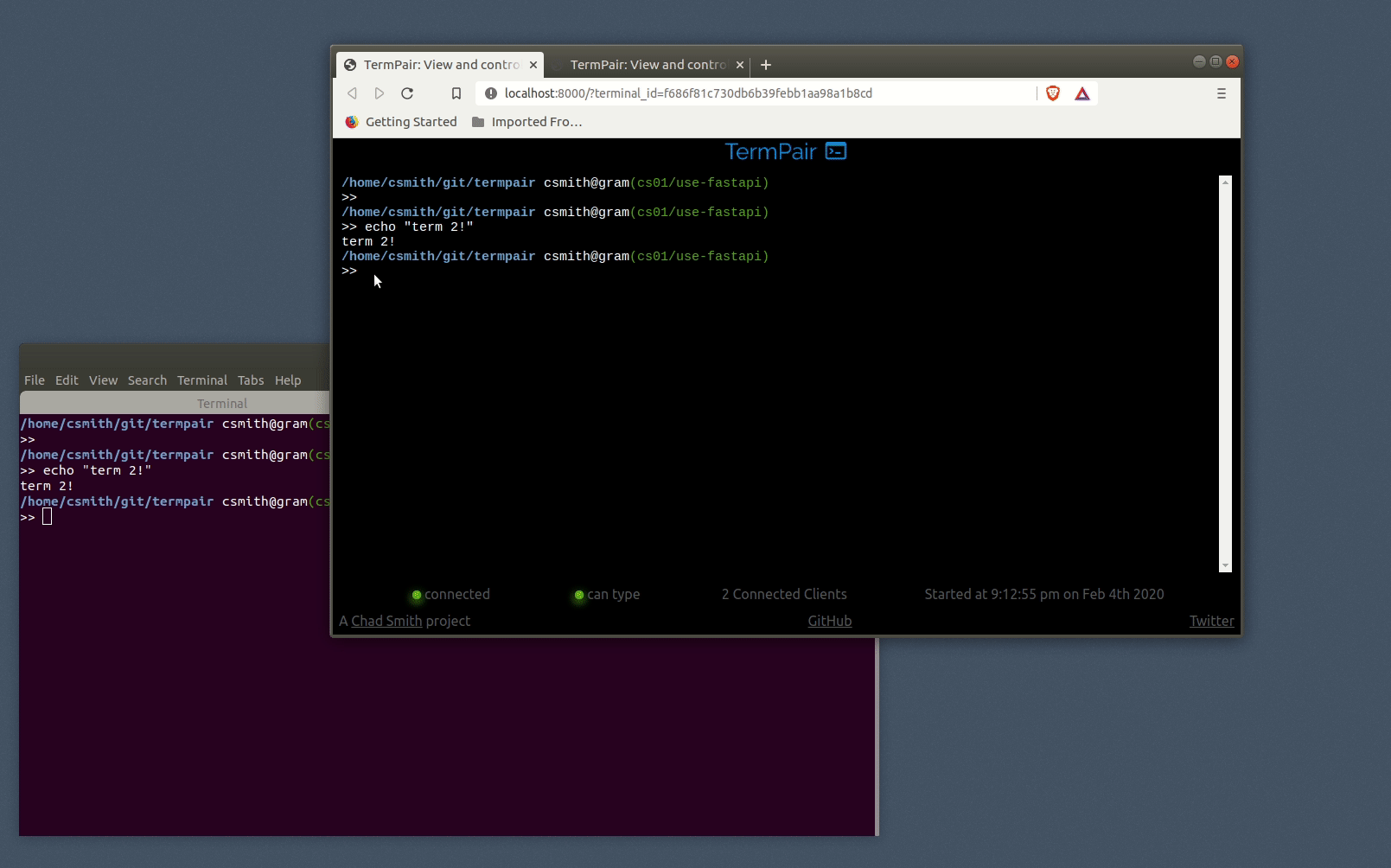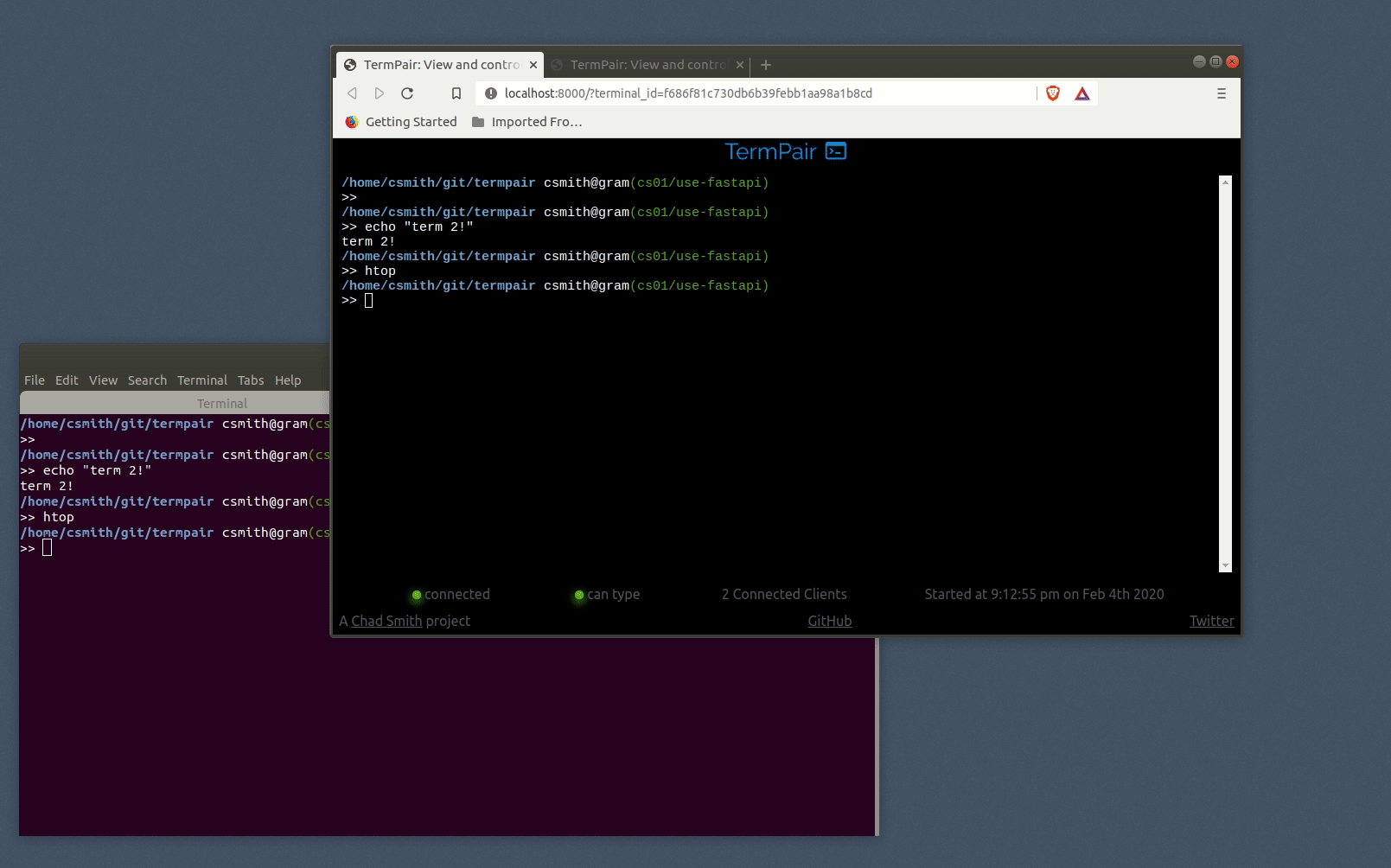
The server multicasts terminal output to all browsers that connect to the session.
Security
TermPair uses 128 bit end-to-end encryption for all terminal input and output.
The browser must be running in a secure context. This typically means running on localhost, or with secure http traffic (https).
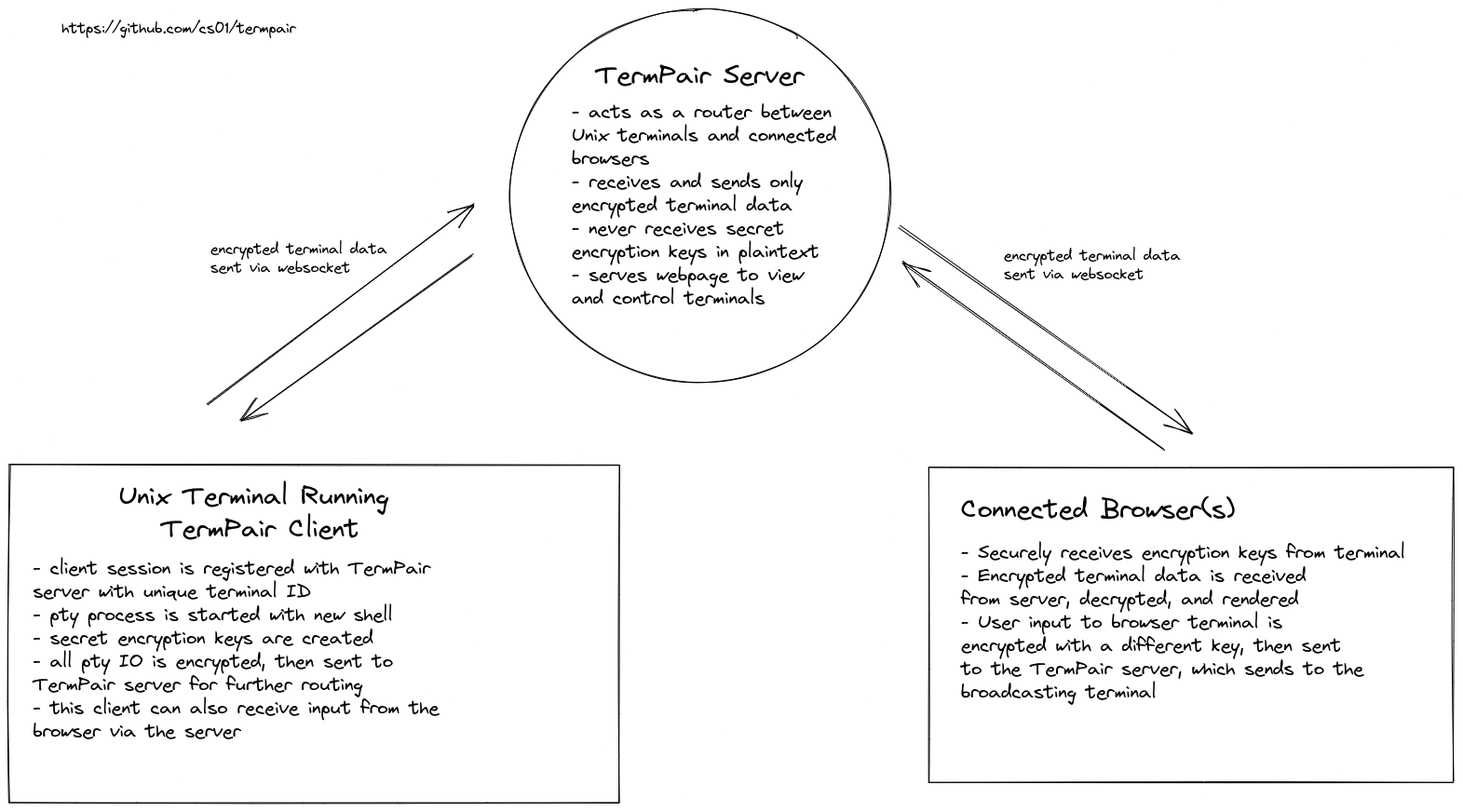
How it Works
TermPair consists of three pieces:
- terminal client
- server
- browser client(s)
First, the termpair server is started (termpair serve). The server acts as a router that blindly forwards encrypted data between TermPair terminal clients and connected browsers.
It listens for termpair websocket connections from unix terminal clients, and maintains a mapping to any connected browsers.
Before the TermPair client sends terminal output to the server, it encrypts it using a secret key so the server cannot read it. The server forwards that data to connected browsers. When the browsers receive the data, they use the secret key to decrypt and display the terminal output. The browser obtains the secret key via a part of the url that is not sent to the server.
Likewise, when a browser sends input to the terminal, it is encrypted in the browser, forwarded from the server to the terminal, then decrypted in the terminal by TermPair, and finally written to the terminal's input.
Run With Latest Version
Use pipx to run the latest version without installing:
Serve:
> pipx run termpair serve
Then share:
> pipx run termpair share --open-browser
Installation
You can install using pipx or pip:
> pipx install termpair
or
> pip install termpair
CLI API
> termpair --help
usage: termpair [-h] [--version] {share,serve} ...
View and control remote terminals from your browser
positional arguments:
{share,serve}
optional arguments:
-h, --help show this help message and exit
--version
To start the TermPair server:
> termpair serve --help
usage: termpair serve [-h] [--port PORT] [--host HOST] [--certfile CERTFILE]
[--keyfile KEYFILE]
Run termpair server to route messages between unix terminals and browsers. Run
this before connecting any clients. It is recommended to encrypt communication
by using SSL/TLS. To generate an SSL certificate and private key, run `openssl
req -newkey rsa:2048 -nodes -keyout host.key -x509 -days 365 -out host.crt`.
To skip questions and use defaults, add the `-batch` flag. You can ignore
warnings about self-signed certificates since you know you just made it. Then
use them, pass the '--certfile' and '--keyfile' arguments.
optional arguments:
-h, --help show this help message and exit
--port PORT, -p PORT Port to run the server on (default: 8000)
--host HOST Host to run the server on (0.0.0.0 exposes publicly)
(default: localhost)
--certfile CERTFILE, -c CERTFILE
Path to SSL certificate file (commonly .crt extension)
(default: None)
--keyfile KEYFILE, -k KEYFILE
Path to SSL private key .key file (commonly .key
extension) (default: None)
To share a terminal using the TermPair client:
> termpair share --help
usage: termpair share [-h] [--cmd CMD] [--port PORT] [--host HOST]
[--no-browser-control] [--open-browser]
Share your terminal session with one or more browsers. A termpair server must
be running before using this command.
optional arguments:
-h, --help show this help message and exit
--cmd CMD The command to run in this TermPair session. Defaults
to the SHELL environment variable (default: /bin/bash)
--port PORT, -p PORT port server is running on (default: None)
--host HOST host server is running on (default: http://localhost)
--no-browser-control, -n
Do not allow browsers to control your terminal
remotely (default: False)
--open-browser, -b Open a browser tab to the terminal after you start
sharing (default: False)
System Requirements
Python: 3.6+
Operating System:
- To view/control from the browser: All operating systems are supported.
- To run the server,
termpair serve: Tested on Linux. Should work on macOS. Might work on Windows. - To share your terminal,
termpair share: Tested on Linux. Should work on macOS. Probably doesn't work on Windows.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
File details
Details for the file termpair-0.1.1.0.tar.gz.
File metadata
- Download URL: termpair-0.1.1.0.tar.gz
- Upload date:
- Size: 536.3 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/3.4.1 importlib_metadata/4.4.0 pkginfo/1.7.0 requests/2.25.1 requests-toolbelt/0.9.1 tqdm/4.61.0 CPython/3.8.9
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 5bcf0591ef9b71780536253899ac9d3d383474293a412898f640955825cfae86 |
|
| MD5 | 784b6a209243ed4780502714c7663783 |
|
| BLAKE2b-256 | 502117012f5a7c0b1be6cce1204f42996050c8ca2fd3d535ea466be3bd0e2731 |
File details
Details for the file termpair-0.1.1.0-py3-none-any.whl.
File metadata
- Download URL: termpair-0.1.1.0-py3-none-any.whl
- Upload date:
- Size: 542.7 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/3.4.1 importlib_metadata/4.4.0 pkginfo/1.7.0 requests/2.25.1 requests-toolbelt/0.9.1 tqdm/4.61.0 CPython/3.8.9
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | e13d5c2ec788b7014af78175703507c30d38f69b6627d70d8718f87ea2bd66cd |
|
| MD5 | dc82e614cd4a3fc5ffb087b47d72eb46 |
|
| BLAKE2b-256 | ca1dca51a011d5a17cff9b5da72b50a7daa1e2f091d1a2a6bcc469cb814dd1c3 |